Over 35+ years ago, the internet was a much safer environment. So now DNS based attacks are still being used & and is a big problem for some organizations.
With an unreliable protocol such as UDP for transport, you opening the door for spoof'd flood attacks to a victim network.
Next, UDP/TCP is support for DNS over port 53 but no privacy. Anybody can peek at your traffic and analyze your traffic patterns based on just DNS query/response between client-server.
DNScrypt and DNSSEC was two attempts to secure DNS but these dropped from popularity. DNScurve was also an alternative. I wrote about this over 5 years ago.
Two current method that's available & that address both issues comes up as ;
DoH or DoT ( DNS Over HTTP or DNS Over TLS)
Cloudflare / Google and a few others have support for bothservices and these can prevent and protect dns-data traffic.
You can make a simple dns query to cloudflare over http for testing.
Both { DoH| DoT } uses TLS for encryption , the over head would be much higher but at the benefit of security and protection from spoof attacks. It's nice to know with cloudflare and GooG they only handle HTTPS and not HTTP.
A DNS-2-DoH server could allow you to integrate these functions with little impact to internal hosts as far as integration since DoH is a simple HTTP.GET
example
For cloudflare; you must set application type of JSON for proper response if not they will deliver a 4XX response. Goog does not enforce that requirement and ignore that header.
FWIW: Google seems to be much simpler for DoH queries
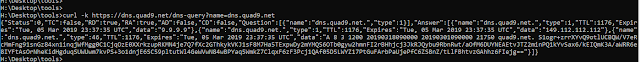
quad9 ( 9.9.9.9 ) has been supporting DNSoverHTTP
NOTE: I'm very disappointed that OpenDNS now { Umbrella }; does not support DoH or DoT and has no plan to do so !
NSE ( network security expert) and Route/Switching Engineer
kfelix -----a----t---- socpuppets ---dot---com
^ ^
=( @ @ )=
o
/ \









No comments:
Post a Comment